- Home /
- ACCESS CONTROL /
- ELECTRO MECHANICAL /
- CYBERLOCK /
- MINI AUTHORISER KEYPORT
Shop Now
- ACCESS CONTROL
- ALARM SYSTEMS
- AUTOMOTIVE SECURITY
- CCTV
- DOOR HARDWARE
- ELECTRONIC LOCKING
- EMERGENCY SERVICES LOCKS
- INTERCOM SYSTEMS
- KEY BLANKS
- KEYS & ACCESSORIES
- LOCK CYLINDERS
-
LOCKS
- AUTOMOTIVE LOCKS
- BOLTS
- CAM LOCKS & ACCESSORIES
- CUPBOARD LOCKS & ACCESSORIES
- DEADLOCKS
- DEADLOCKS ACCESSORIES
- DOMESTIC
- ENTRANCE LOCKS
- GARAGE LOCKS & ACCESSORIES
- KEY IN KNOB
- KEY IN LEVER
- LOCKS SPARE PARTS
- MECHANICAL DIGITAL LOCKS
- MORTICE LOCKS
- POOL AND GATE LOCKS
- SCREEN DOOR LOCKS
- SLIDING DOOR LOCKS AND ACCESSO
- WINDOW LOCKS AND ACCESSORIES
- LOCKSMITH TOOLS
- MECHANICAL
- NETWORKING TOOLS
-
PADLOCKS & ACCESSORIES
- ABUS PADLOCKS
- CABLES & CABLE LOCKS
- CHAIN
- HASP & STAPLES/PADBOLTS
- LUGGAGE LOCKS
- PADLOCK ACCESSORIES
- PADLOCKS
- WYNNS 30MM PADLOCK
- WYNNS 40MM PADLOCK
- WYNNS 50MM PADLOCK
- WYNNS 6 PIN 40MM PADLOCK
- WYNNS 6 PIN 45MM PADLOCK
- WYNNS 6 PIN 50MM PADLOCK
- WYNNS 6 PIN 55MM PADLOCK
- WYNNS COMBINATION PADLOCK
- WYNNS PADLOCKS
- SAFES
- SECURITY EDGE
- SECURITY EDGE 5 PIN EURO CYLIN
- SECURITY EDGE BARRELS
- SECURITY EDGE L SERIES CYLINDE
- SECURITY EDGE L SERIES PADLOCK
- SECURITY EDGE PRODUCTS
-
SECURITY EDGE S SERIES CYLINDE
- 001 S SERIES INNER CYLINDERS
- 201 S SERIES ROUND CYLINDERS
- 355 S SERIES INNER CYLINDERS
- 530 S SERIES KNK CYLINDERS
- 570 S SERIES OVAL CYLINDERS
- 670 S SERIES CAM LOCKS
- 8090 S SERIES TRILOCK CYLINDER
- 8217/5 S SERIES ASTRA OVAL CYL
- 8221 S SERIES PD CYLINDERS
- 8466 S SERIES KAWNEER CYLINDER
- EURO S SERIES FIXED CAM CYLIND
- EURO S SERIES FIXED CAM MODULA
- EURO S SERIES LAZY CAM CYLINDE
- SECURITY EDGE S SERIES PADLOCK
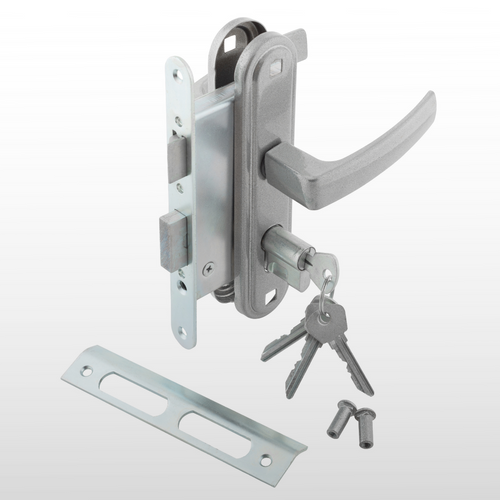
MINI AUTHORISER KEYPORT
Description
Communicator, indoor/outdoor installation
The Mini-Keyport is a wall-mounted device that connects directly to the Authorizer Hub. It is a user interface device that includes a CyberKey port. It can be installed in remote areas without a computer (inside or out) such as a hallway or employee entrance.
Power/Hardware Connection:
- Power supplied by Web Authorizer Hub
Required Hardware:
- The Mini-Keyport connects directly to an Authorizer Hub
Compatible CyberKey Smart Keys:
- The Mini-Keyport is compatible with CK-IR7C, CK-IR7, CK-RBT, CK-RCG, CK-RXD, and CK-RXD2 CyberKey smart keys.
Communicators Overview:
- CyberLock communication devices serve as the interface between CyberLock hardware and CyberAudit management software.
Access privileges are distributed to key holders via communicators. These devices are linked to the software over a local area network or securely over the Internet. When a CyberKey and communicator make contact, the audit trail is downloaded from the key while simultaneously new schedules, permissions, and system information are uploaded to the key.
To increase security and accountability, access privileges can be programmed to expire at scheduled intervals. This results in users regularly updating and reauthorizing keys at communicators.
Communicator Features:
- Key activity downloads and key permission updates occur simultaneously.
- Communicator compatibility depends on the key type and version of CyberAudit software installed.
- Several communicators offer multiple functions, such as charging the key battery or storing unprogrammed keys.